The results
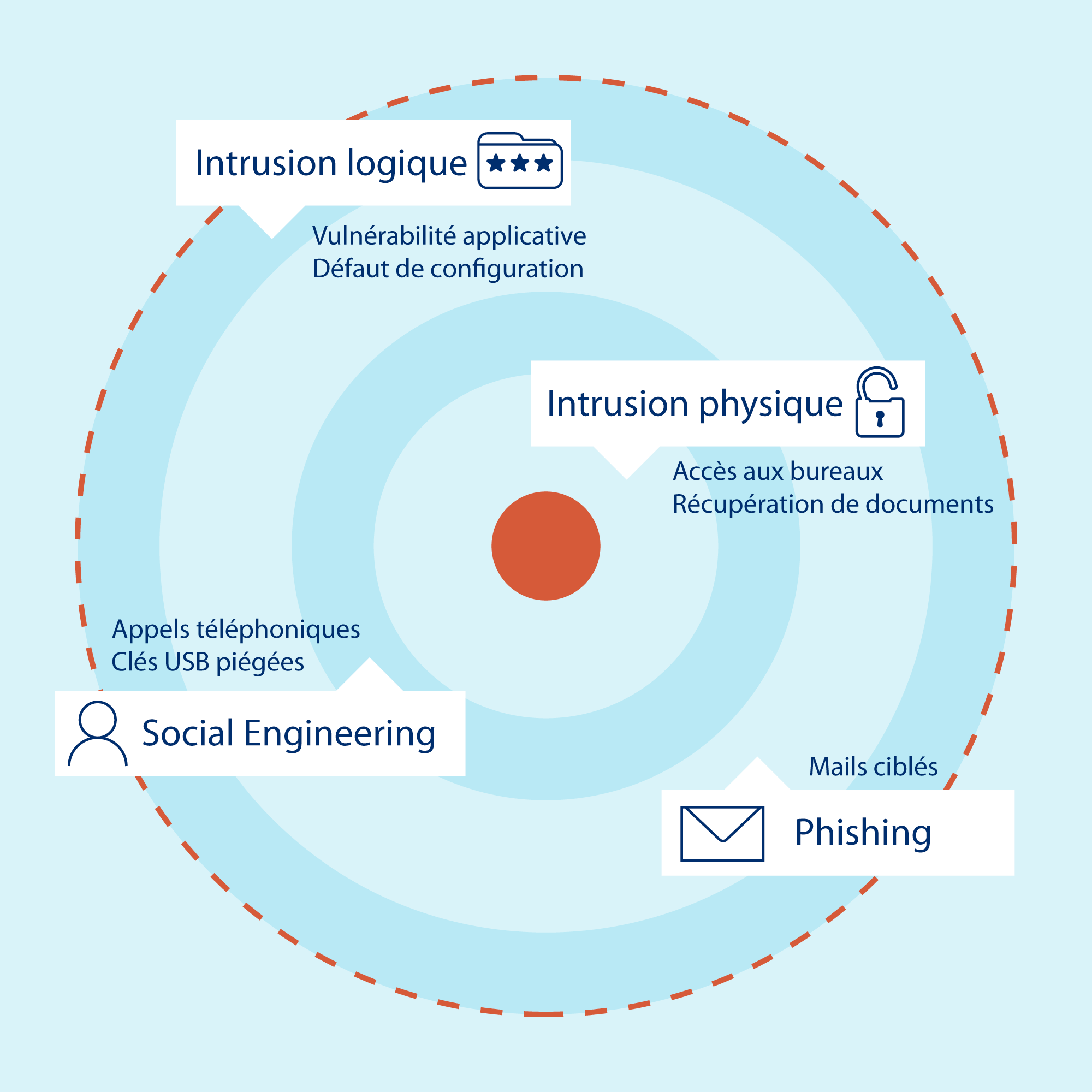
The different attack vectors
-
physical intrusion
Our consultants will try to physically access your infrastructures (offices, datacenter, etc.) to connect directly to the internal network in a resilient way or to retrieve information (documents, etc.).
-
External intrusion
Your entire Information System exposed to the Internet potentially constitutes a gateway to your internal network. As such, we will passively and actively seek to identify a vector of compromise / rebound.
-
social engineering
All interactions with your collaborators can be used to develop the mission. In this context, false telephone calls, appointments, interventions, deposits of USB keys in places accessible to the public, etc. can be implemented.
-
Phishing
Your employees will be targeted by Phishing emails aimed at recovering sensitive information such as identifiers in order to continue the operation of the mission.


