-
Toutes les catégories
- Active Directory
- PCI DSS
Part 5 : Machine Accounts in the Active Directory
In this article, we will focus on the machine accounts in the Active Directory within its NTDS database. As mentioned in the fourth part of this article series, machine accounts are easily identifiable by the presence of the “$” character at the end of the account name(1).
Just like a user needs an account to authenticate with the Active Directory service and access its resources, a machine (workstation, server, printer, etc.) also needs an account to be a member of the domain.
Creation of a Machine Account
When a workstation is joined to the domain, an account is automatically created in the NTDS database. This account is quite similar to a user account and has a password. However, the password is randomly generated by the Active Directory service and is changed by default every 30 days.
Note : If a workstation has not connected to the domain for more than 30 days, the next authentication to the domain will be allowed, and the password will be renewed.
Adding a machine to the domain can be done in two ways:
- From the machine being enrolled in the domain: This requires an administrator to log in to the workstation and add the machine to the domain. The account will be created in the Active Directory and by default, it will be included in the “Computers” Organizational Unit (OU). However, logging in to the workstation for domain joining is not recommended because the account adding the machine to the domain will become the owner of the machine with privileged rights. To avoid this “owner” type of control of the machine account, it is recommended to perform an offline domain join using the “Djoin” utility.
Note : Control paths in Active Directory are an aggregation of “control relationships” between domain entities (users, computers, groups, GPOs, containers, etc.), which aim to answer questions such as “Who can obtain ‘Domain Admins’ privileges?”, “What resources can a user control?”, or even “Who can read the CEO’s emails?”. We will address the topic of control paths and their identification in an upcoming article in this series.
- Pre-stage or pre-created machine accounts: These accounts are created before the machine exists. This process is commonly used by deployment solutions and allows for better control of machine addition to the Active Directory. This option is highly favored in enterprises as it allows the new machine to be directly included in the appropriate OU and apply corresponding GPOs.
Sometimes, the password stored on the machine and the password stored in the NTDS database may differ. The machine becomes desynchronized and can no longer authenticate. A password reset operation is required. The PowerShell command “Reset-ComputerMachinePassword” (2) can be used for this purpose.
Properties of machine accounts
Similar to user accounts, machine accounts have numerous attributes in the NTDS database. Many attributes are shared with user accounts, such as sAMAccountName, objectSID, group, logoncount, description, whenCreated, etc. However, there are specific attributes for machine accounts, such as the operating system name (operatingSystem), its version (operatingSystemVersion), or service pack (operatingSystemServicePack).
To determine the nature of each machine in the Active Directory, it is also necessary to examine the active properties present in the UserAccountControl (UAC) on the associated account. Active properties are referenced by a hexadecimal value. Therefore, to determine the number of active values, a mask needs to be applied. Here are the UAC properties that are relevant for machine accounts. The complete list of properties is available at the following address : https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/useraccountcontrol-manipulate-account-properties
| Name | Hexadecimal Value | Role | Note |
| ACCOUNTDISABLE | 0x00000002 | Indicates that the machine account is disabled. A workstation with this characteristic can no longer connect to the domain. | When an employee returns their workstation or a server is decommissioned, it is common to disable the associated account before deletion. |
| LOCKOUT | 0x00000010 | Indicates that the machine account is locked. A workstation with this characteristic can no longer connect to the domain. This is relatively rare for machine accounts. | The locking of a machine account is very uncommon in a production domain. |
| PASSWD_NOTREQD | 0x00000020 | Indicates that no password is required. However, this doesn’t mean the absence of a password. | When a machine account is created, this attribute is set and disappears once the machine joins the domain. It’s not uncommon to still see this attribute on domain machine accounts, usually due to the use of third-party identity management software that forgets to remove this property during account creation. |
| INTERDOMAIN_TRUST_ACCOUNT | 0x00000800 | Indicates that it is an interdomain trust account. | The number of accounts with this property indicates the number of interdomain trust relationships. |
| WORKSTATION_TRUST_ACCOUNT | 0x00001000 | Indicates that it is a server, workstation, or another network device enrolled in AD. | For the majority, these accounts are Windows servers in the infrastructure and user workstations. Other accounts may be file servers, printers, or other types of equipment. |
| SERVER_TRUST_ACCOUNT | 0x00002000 | Indicates that it is a domain controller. | This property is generally associated with TRUSTED_FOR_DELEGATION and should only be enabled on domain controllers. |
| DONT_EXPIRE_PASSWORD | 0x00010000 | Indicates that the password never expires. | This property is generally used on non-Windows equipment machine accounts that don’t support automatic password change mechanisms. Passwords for these accounts must be strong. |
| MNS_LOGON_ACCOUNT | 0x00020000 | Indicates that the account is an MNS (Majority Node Set) account. | This type of account is almost never encountered and is required for cluster node operations for servers. |
| TRUSTED_FOR_DELEGATION | 0x00080000 | Indicates that the machine supports unconstrained Kerberos delegation. This mechanism allows the server to impersonate the user and authenticate on their behalf to another service (impersonation). | From a security perspective, only domain controllers should have this property. Approving other machines is an operation with significant security implications and should only be done when necessary. We’ll explore delegations further in another article. |
| NOT_DELEGATED | 0x00100000 | Indicates that the user account cannot be delegated. | By default, no account has this attribute. Restricting delegation for sensitive accounts, especially administrative ones, is a highly recommended security measure. |
| PASSWORD_EXPIRED | 0x00800000 | Indicates that the password has expired. | Machine account passwords never expire (they are automatically renewed). Only very specific cases, such as non-Windows machines (e.g., a NAS), might have this attribute. |
| TRUSTED_TO_AUTH_FOR_DELEGATION | 0x01000000 | Indicates that the machine can impersonate a client’s identity and authenticate itself as such to other remote servers in the network (protocol transition). | Only RODCs are supposed to have this property. It’s a very sensitive security aspect and should only be set for accounts where absolutely necessary. |
| PARTIAL_SECRETS_ACCOUNT | 0x04000000 | Indicates that the server is a Read Only Domain Controller (RODC). | Only RODCs are supposed to have this property. |
Securing Machine Accounts
Most machine accounts have a strong password generated automatically and randomly every 30 days. However, equipments that are incompatible with this mechanism (typically non-Windows systems) rely on manually set passwords, which may be weak. These passwords are stored like user accounts in either NT format or, in some cases, LM format (see the article on passwords[FD1] ).
Note : In older Active Directories, it is possible to find accounts marked as “Assign this computer account as a pre-Windows 2000.” The password for these machine accounts is the lowercase name of the machine account itself. For example, the password for the machine account “XMCO$” would be “xmco”.
The theft of a machine account can enable reconnaissance activities (e.g., browsing authenticated shares), initiate various attacks (3) on the Active Directory, or establish persistence (4).
During our IAMBuster analyses, it is common to identify a few machine accounts that rely on weak passwords. We also pay close attention to last login dates and OS versions to identify active outdated systems or those that may be out of sync.
Graphes
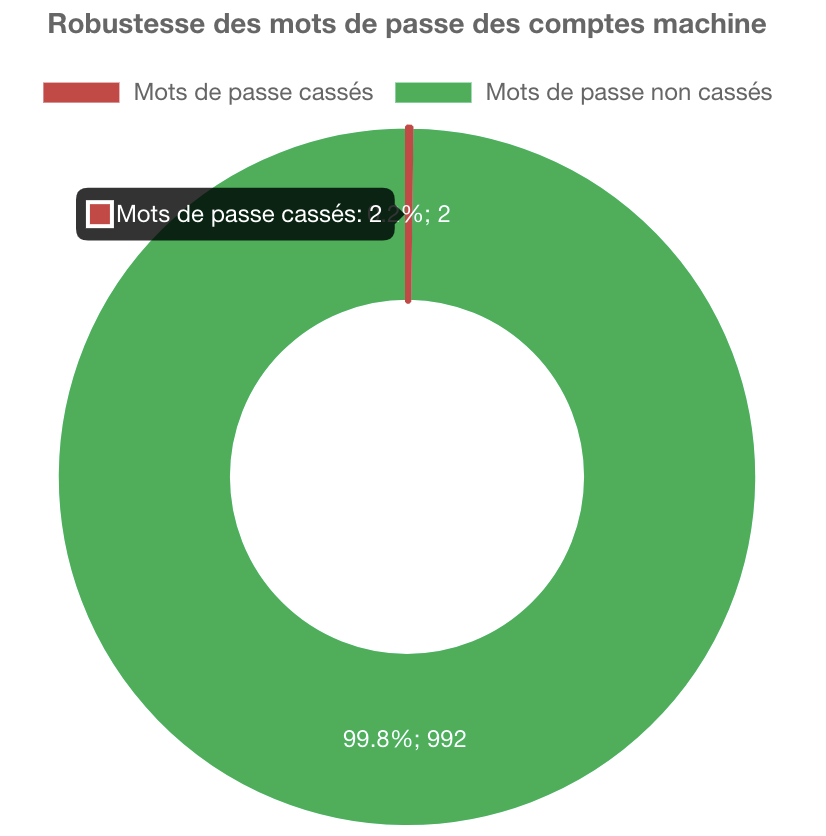
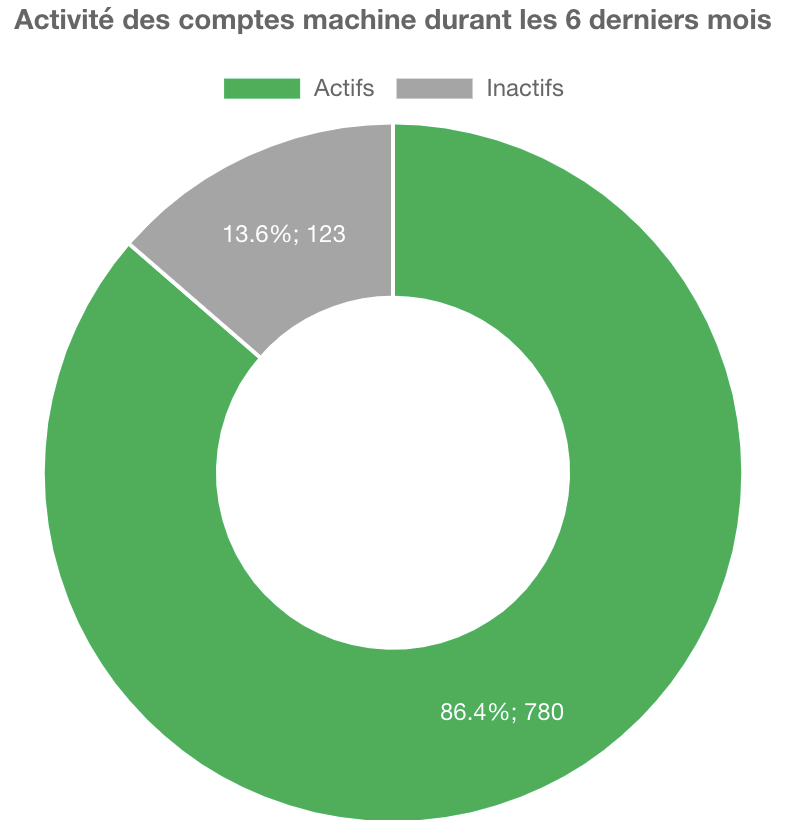
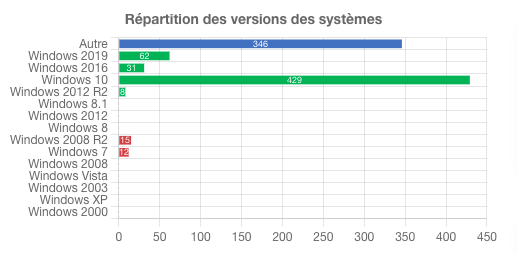
Note : By default, any domain user with local administrator rights on their computer has the ability to join up to 10 machines to the domain. This results in the creation of a machine account in the Active Directory. However, this functionality can also facilitate the exploitation of certain vulnerabilities (CVE-2021-42278 / CVE-2021-42287). Therefore, it is recommended to verify that the ms-DS-MachineAccountQuota attribute on the domain is set to zero.
From a logging perspective, event 4741, which corresponds to the creation of a machine account in the domain, can be monitored.
The properties of machine accounts are therefore as important as those of user accounts, and auditing them regularly helps identify configuration flaws that could aid attackers in their work.
References
1. gMSA (Group Managed Service Account) accounts also end with “$”. However, the different properties discussed in this article make it easy to differentiate them.
3.https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/resource-based-constrained-delegation#performing-a-complete-s4u-attack
https://pentestlab.blog/2022/02/01/machine-accounts/
https://securityboulevard.com/2022/06/elevating-privileges-with-authentication-coercion-using-dfscoerce/
4. https://pentestlab.blog/2022/01/17/domain-persistence-machine-account/


